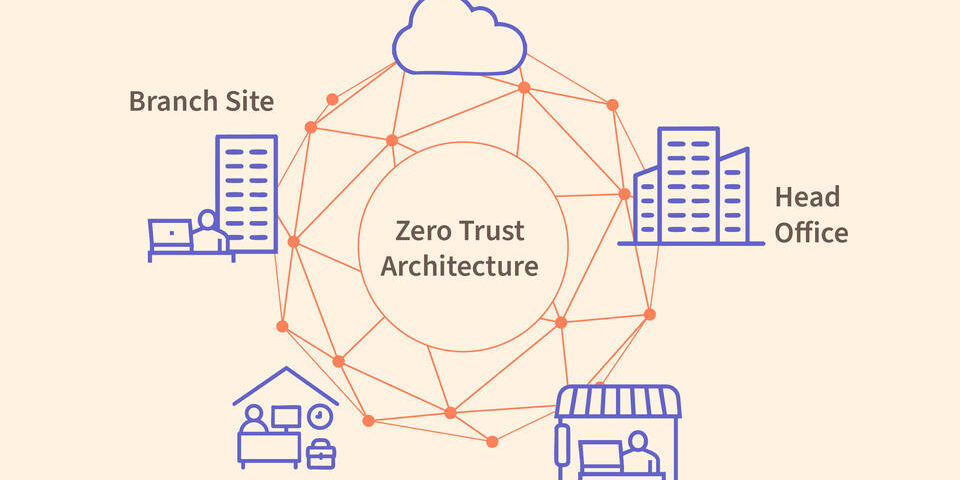
If you’re trying to secure your organization’s computer network from cyberattacks, traditional approaches may not work. Gone are the days when you could keep all your electronic assets inside a single building and construct a firewall between them and the wider internet. Now you have remote workers logging in from distant cities and cloud-based software applications running elsewhere in a data center. You’ve heard that your best bet for protecting all these far-flung assets is to create a zero trust architecture (ZTA), which assumes that no user or device can be trusted, regardless of its location or previous verification.So how do you start?Helping answer that question is the goal of newly finalized guidance from the National Institute of Standards and Technology (NIST). Implementing a Zero Trust Architecture (NIST Special Publication (SP) 1800-35) shows you how others have built ZTAs so that you can build your own. Developed through a project at the NIST National Cybersecurity Center of Excellence (NCCoE), the publication offers 19 example implementations of ZTAs built using commercial, off-the-shelf technologies. It also offers results and best practices from the 24 industry collaborators who participated in the project.“Switching from traditional protection to zero trust requires a lot of changes. You have to understand who’s accessing what resources and why,” said Alper Kerman, a NIST computer scientist and co-author of the publication. “Also, everyone’s network environments are different, so every ZTA is a custom build. It’s not always easy to find ZTA experts who can get you there.”Older approaches to network security rely on the idea of a perimeter, where once a device gains entry it can then freely access the network’s internal data, applications and other resources. This perimeter idea, developed when many networks were limited to a single location such as a building or campus, is growing obsolete. Nowadays a single organization may operate several internal networks, use cloud services, and allow for remote work — meaning there is no single perimeter. READ MORE

Maximize your earnings with top-tier offers—apply now! https://shorturl.fm/S89MR
Start earning on every sale—become our affiliate partner today! https://shorturl.fm/0xkZe
Earn up to 40% commission per sale—join our affiliate program now! https://shorturl.fm/Sjfq9
Turn your audience into earnings—become an affiliate partner today! https://shorturl.fm/9PRkh
Maximize your income with our high-converting offers—join as an affiliate! https://shorturl.fm/Zmgi2
Boost your income effortlessly—join our affiliate network now! https://shorturl.fm/iD4vS
Sign up for our affiliate program and watch your earnings grow! https://shorturl.fm/JcNPV
Become our affiliate—tap into unlimited earning potential! https://shorturl.fm/6tjly
Earn up to 40% commission per sale—join our affiliate program now! https://shorturl.fm/Eubxn
Unlock exclusive rewards with every referral—apply to our affiliate program now! https://shorturl.fm/7a4pQ
Drive sales, earn big—enroll in our affiliate program! https://shorturl.fm/w4dRE
Join our affiliate family and watch your profits soar—sign up today! https://shorturl.fm/W8kmj
Start earning every time someone clicks—join now! https://shorturl.fm/5JHWr
Share our offers and watch your wallet grow—become an affiliate! https://shorturl.fm/OG3B3
Join our affiliate community and maximize your profits—sign up now! https://shorturl.fm/Cy1Lk